Logic Gates
Binary is the foundation of all computer systems. It is the simplest form of script made up of solely 1s and 0s. There are also different processors called gates:- AND gates require both inputs to be set as 1 for the output to be 1.
- OR gates require at least 1 of the inputs to be 1 for the output to be 1.
- NOT gates only have a single input, they output the opposite of the input.
These are the simplest form of gates, examples are displayed below.
AND Gates
NOT Gates
OR Gates
AND NOT Gates
Binary
Binary is a numerical system in base 2. This means it represents numerical values using two symbols, in this case 1 and 0. A single number is a bit, a group of four numbers is a nibble and a full eight numbers is a byte. A zero represents nothing and a one represents a number, which go up in powers of two. Therefore a number 9 in binary will be:
8421
1001
as 8+0+0+1=9.
More can be found here.
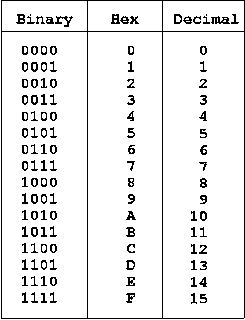
Hex
Also known as hexadecimal, hex is a base 16 numerical system. The first unit represents a multiple of 16 and the second is a number added to the first. The second unit can be a number up to 9 or a letter up to F. 1-9 stand for themselves and A-F represent the next numbers to 15.
ASCII
ASCII (American Standard Code for Information Interchange) is a set of 127 characters (95 printable and 35 not) and the null code (00000000) devised by the American Standards Association for use as the main characters in telegraphs. It originally used 7 bits but as 8 bit computers became the norm, it was extended to 8 bits so 128 more characters could be added. One character is one byte.
Instruction Sets
An Instruction set is a list of all of the instructions needed in a computer for a processor to execute. These will usually include common mathematical processes, logic gates, data instructions (such as move, input, load and store) and control flow instructions.These lists are different for each brand of processor and sometimes each generation. These instructions are stored in binary and the CPU has to decode them so it knows what to do. There is two parts of an instruction, the operator and operand. The operator tells the CPU what to do. and the operand tells the CPU what to apply the operation to.
Sound
Sound is an analogue energy form. To store it on a computer we need to convert it into a digital one. To do this we measure the frequency/loudness etc at equal intervals. These are called samples. The bit rate is the number of bits sampled in a given time. Sound files are often quite large, this means we often have to compress them into a file format like MP3. Algorithms are devised to remove parts of the data people are least likely to hear.
Images
Binary data can represent images and store them as bits. Pictures are shown as a series of coloured pixels. The metadata is located at the start of the image in binary and give information such as resolution, colour depth, width and height. Without this the image would simply be a string of ones and zeros. Colour depth is the number of colours that can be represented in the image. A depth of 1 bit will represent 2 colours (1 and 0). 2 bits allows 4 colours and so on. These are called bit mapped images. You can also store an image as a vector graphic. This defines them as formulae and define the points, lines and curves of the image rather than storing them as pixels. This means they can be enlarged without being distorted as the image is simply recalculated rather than enlarging each pixel.
Development Software
You need certain pieces of software to develop software. These are used to write the code that makes the program work.
Editors:
These are usually a cut down word processors that save the words but not the formatting. We use these to write the main operations of the program. You can also use software that utilises "pretty printing". This will detect things like loops, variables etc. Some will even add line numbering to help with debugging.
Compilers:
These will convert high level level languages into machine code the CPU can run. You will need a different compiler for each programming language (e.g python etc.)
Interpreters:
Interpreters do a similar function to compilers although they do it a line at a time and execute as they go. This uses a lot more RAM and you need the correct interpreter if you ever want to run the program. It is also slower. e.g. C++
Assemblers:
Assembly language is a convenient way to write base machine code that isn't in binary. It uses a set of mnemonics to represent machine operations and is specific to the processor it runs on.
Linkers:
Linkers are for 'glueing' modules of an application written by separate programmes in separate languages to make sure there are no conflicts.